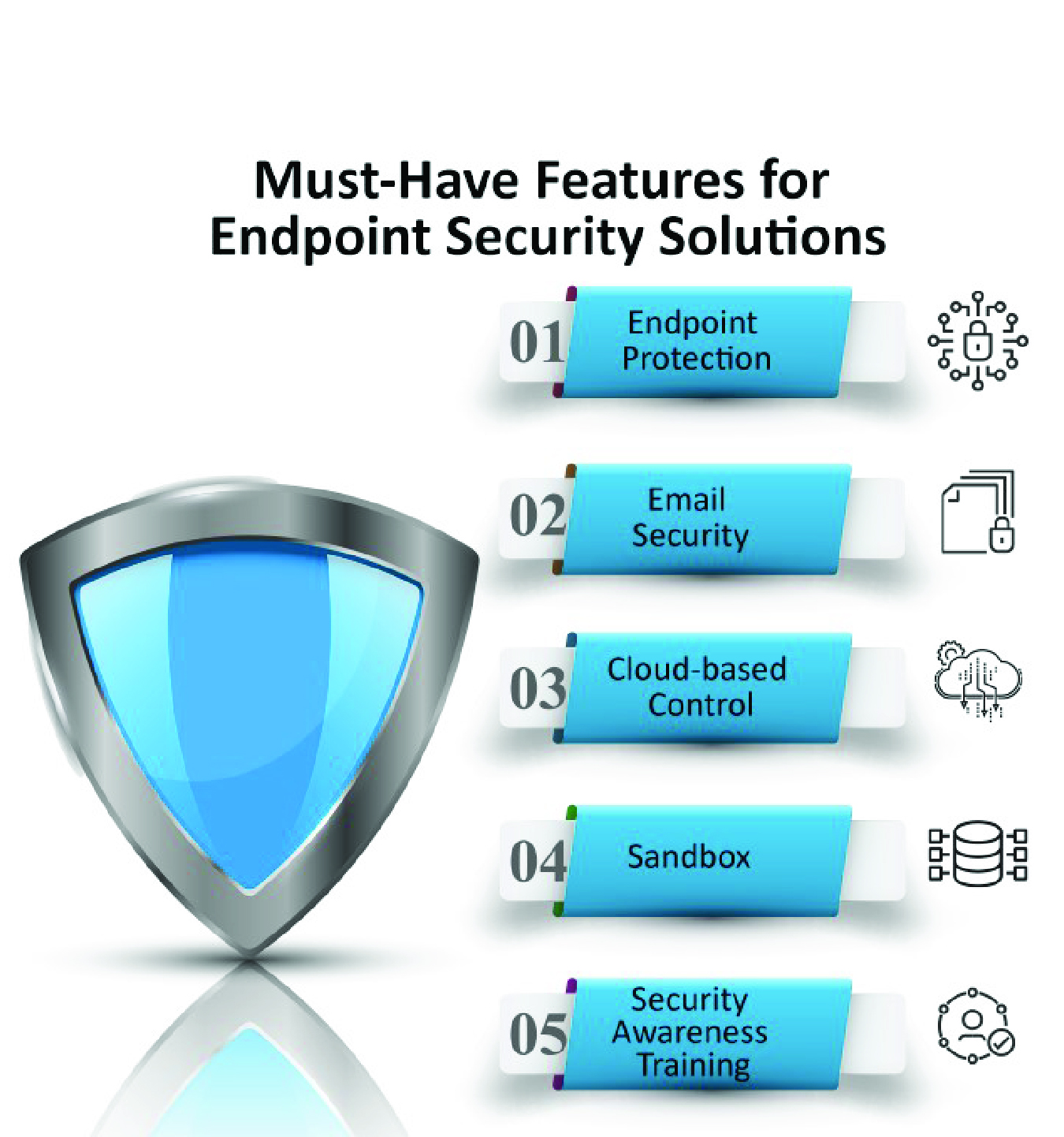
Comprehensive Security Suite with Centralized Management
Multi-Layered Security Approach:
Our endpoint protection solution includes a comprehensive suite of security tools designed to provide robust defense against a wide range of cyber threats. This suite includes antivirus, anti-malware, firewall, intrusion detection systems, and more. Each tool plays a specific role in protecting your endpoints, and together, they create a formidable barrier against cyber attacks.
Centralized Management Console:
Managing endpoint security across an organization can be complex, especially as the number of devices grows. Our centralized management console simplifies this process by allowing you to oversee and control all security measures from a single interface. This console provides a holistic view of your network's security status, enabling you to monitor, manage, and update security protocols across all endpoints efficiently.
Detailed Reporting and Analytics:
Our solution includes advanced reporting and analytics features that provide insights into the security posture of your organization. You can generate detailed reports on various aspects of endpoint security, such as threat detection, response times, and compliance with security policies. These insights help in identifying potential vulnerabilities and making informed decisions to enhance your security measures.
Regular Updates and Patch Management:
Keeping your systems updated is crucial for maintaining security. Our service includes regular updates and patch management for all your endpoints, ensuring they are protected against the latest threats. We manage and deploy updates seamlessly, minimizing disruption to your operations while keeping your security measures current.